Exercise Caution when installing Java Updates
Caution when installing Java Updates is required or you may be tricked into installing FoistWare.
What is FoistWare (also called CrapWare)?
Firstly, lets explain what we mean by FoistWare. FoistWare is a tactic used by software developers to install additional software during the installation process, sometimes without the users knowledge or consent or with deceptive messages that trick the user into installing the additional software.
Often if you accept the default installation options, the unrelated third-party software is installed.
The FoistWare itself may be a legitimate program, though the manner in which it is installed makes it FoistWare.
The software developers try to make a quick buck by tricking users into installing software they don’t need, which can impact on system performance.
Some FoistWare applications are browser hijacks that modify your web browser’s settings without user’s permission, which can inject unwanted advertising, replace your existing home or search pages.
This tactic is sometimes used by Freeware software developers and has been used by Oracle for many years when installing updates to their popular Java software.
What is Java (by Oracle)?
Java is a programming language and computing platform used on many devices from laptops to datacenters, game consoles and mobile phones. Lots of applications and websites will not work unless you have Java installed.
For Australian Accounting firms and Businesses, one especially relevant application that needs Java is the Australian Government’s AUSkey secure login, used to access participating Government websites.
Oracle is at it again installing deceptive software with Java Updates
Java Updates have previously tricked users to install the Google Toolbar, Yahoo and Ask Toolbar and Search App. Here’s one example of what users were prompted with when installing previous Java Updates:
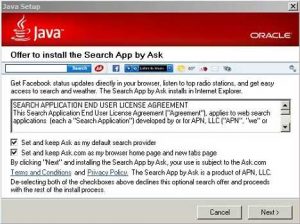
Previous Java Update defaulting to install Ask Search
The latest Java updates now try to trick you into installing the Teoma Search App:
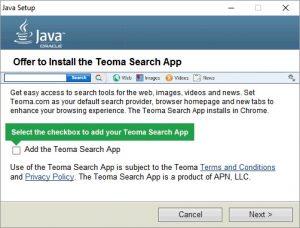
Latest Java Update Install Offer Teoma Search App
Other vendors that have been purveyors of FoistWare include:
- Adobe when you download Flash Player, included Google Toolbar for Internet Explorer or when you download Reader downloaded Google Chrome.
- Skype
Our Recommendations for Caution installing Java Updates
It is important to install patches and updates for all software, including Java. If you don’t install the latest Java update, you may not be able to use your AUSkey to access Government websites.
When installing software, including updates, always review installation questions/options, rather than simply accepting the Defaults and clicking Next, Next, Next.
If you require any assistance with installing updates, removing any unwanted FoistWare inadvertently installed, or removing any browser hijacks, please Contact Us.
See the following articles for more information on Java Updates installing FoistWare: