Is your Windows 10 up to date?
Did you know that as at May 2021, there are twelve different versions of Windows 10 and nine of the earlier versions have reached End of Service?
To ensure your device continues to receive critical monthly security and quality updates that contain protection from the latest security threats, you need to ensure your version of Windows 10 is up to date.
Here’s how to confirm if your version of Windows 10 is up to date.
Windows-as-a-Service
With Windows 10, Microsoft introduced “Windows-as-a-Service”. A new approach to deploy, update and service Windows Operating System. Instead of releasing a new version of Windows every three to five years, as Microsoft did with past iterations (eg. Windows 7, Windows Vista, Windows XP), Microsoft continually update Windows 10. Windows 10 Updates (also called Patches) are categorised as two types: Quality Updates and Feature Updates.
What’s the difference between Windows 10 Quality Updates and Feature Updates?
- Quality Updates are cumulative updates that are released once a month (“Patch Tuesday” is the 2nd Tuesday of the month) and contain critical security patches and other fixes to make Windows 10 more reliable. As they are cumulative, the latest update includes all previous updates that came before it. After the download is complete, Quality Updates can take from 15 minutes up to an hour or so to complete, depending on the performance on the computer, including a restart which is required to complete the updates.
- Feature Updates are major upgrades to a new Version of Windows 10 that contain new functionalities. Feature Updates are released twice a year. After the download is complete, Feature Updates can take between 1 to 4 hours to complete, depending on the performance on the computer, including a restart which is required to complete the updates. Each Feature Update continues to receive Support and Quality Updates for 18 months after its initial release.
Windows 10 Feature Updates
To confirm if your Windows 10 version is up to date:
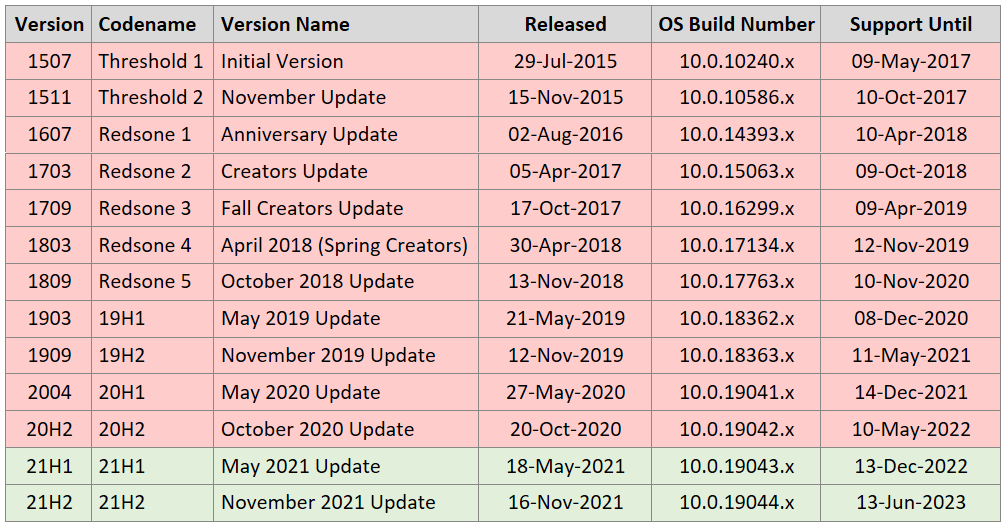
To confirm the current Windows Version and Build of Windows 10 you have installed: Start > WinVer > Enter. To check if your version of Windows 10 is up to date and your device in continuing to receive critical monthly security and quality updates, find your version in the above table and check the Support Until date. If you have Version 1909 or prior, we strongly recommend updating to the latest Version of Windows 10.
Windows End of Life, End of Support and End of Service
In recent times, there has been a reasonable amount of publicity (and hype) surrounding previous Microsoft Desktop Operating Systems (Windows 7, Windows XP) reaching End of Life (EOL), which raised awareness that operating systems needed to be upgraded. Windows 7 EOL date (14 January, 2020) was well publicised. After the EOL date, Microsoft ceased providing critical security updates for Windows 7.
The same can’t be said for Windows 10 Versions that have reached End of Service.
Many devices are running old versions of Windows 10 that no longer receive monthly security and quality updates.
Software developers also cease providing support for their software on Operating Systems that have reached EOL.
Proactive Managed IT Support Services
For all iT and Beyond clients who benefit from our Proactive Managed IT Support Services, for continued stability and security, and to minimise disruption and inconvenience to users, we schedule the installation Windows Updates as follows:
- Patch scans are automatically performed Weekly, after normal business hours, during the designated Weekly Maintenance window.
- Quality Updates: If Weekly Patch Scans detect that any Quality Updates are needed, they are automatically installed after normal business hours, during the designated Weekly Maintenance window. This includes restarting workstations if required. We are notified when Servers require a restart to complete patch installations and restart Servers manually after business hours.
- Feature Updates: To allow testing of these major version updates prior to installation, we manually deploy Feature Updates outside of normal business hours at a mutually agreed time, once a year.
For more details:
History and Support End dates
https://en.wikipedia.org/wiki/Windows_10_version_history
Microsoft Windows 10 Update History
https://support.microsoft.com/en-us/topic/windows-10-update-history-1b6aac92-bf01-42b5-b158-f80c6d93eb11